Intune + Microsoft 365 Education Get everything you need to set up, configure, and manage your Windows 10 devices with Intune, included in every Microsoft 365 Education device license. May 27, 2019 Today I would like to share a method to remove the pre-installed Office 365 ProPlus suite from Microsoft Intune managed devices managed with you. Scenario Recently I’ve been deploying a lot of Surface Go’s with Windows Autopilot and Microsoft Intune in an environment where these devices are shared amongst firstline workers. Most of the firstline workers have an Office 365 F1 or Office 365. Mar 27, 2019 Some time ago I wrote a very detailed and long blogpost on how you could control the Office 365 Pro-Plus version and update channel through the ADMX-Backed policy functionality within Microsoft Intune. Intune + Microsoft 365 Education Get everything you need to set up, configure, and manage your Windows 10 devices with Intune, included in every Microsoft 365 Education device license. Get the most value from your Microsoft 365 integrated solution when you use the latest cloud features to help protect users’ privacy and your organization’s data and assets.
Before you can assign, monitor, configure, or protect apps, you must add them to Intune. One of the available app types is Microsoft 365 apps for Windows 10 devices. By selecting this app type in Intune, you can assign and install Microsoft 365 apps to devices you manage that run Windows 10. You can also assign and install apps for the Microsoft Project Online desktop client and Microsoft Visio Online Plan 2, if you own licenses for them. The available Microsoft 365 apps are displayed as a single entry in the list of apps in the Intune console within Azure.
Note
Microsoft Office 365 ProPlus has been renamed to Microsoft 365 Apps for enterprise. In our documentation, we'll commonly refer to it as Microsoft 365 Apps.
You must use Microsoft 365 Apps licenses to activate Microsoft 365 Apps apps deployed through Microsoft Intune. Microsoft 365 Apps for business edition is supported by Intune, however you must configure the app suite of the Microsoft 365 Apps for business edition using XML data. For more information, see Configure app suite using XML data.
Deploying OneDrive through Intune after removal of the native OneDrive client is not supported. If the native OneDrive client is removed, Intune is not able to redeploy OneDrive. Deployment of OneDrive through Intune is not supported.
Before you start
Important
If there are .msi Office apps on the end-user device, you must use the Remove MSI feature to safely uninstall these apps. Otherwise, the Intune delivered Microsoft 365 apps will fail to install.

- Devices to which you deploy these apps must be running the Windows 10 Creators Update or later.
- Intune supports adding Office apps from the Microsoft 365 Apps suite only.
- If any Office apps are open when Intune installs the app suite, the installation might fail, and users might lose data from unsaved files.
- This installation method is not supported on Windows Home, Windows Team, Windows Holographic, or Windows Holographic for Business devices.
- Intune does not support installing Microsoft 365 desktop apps from the Microsoft Store (known as Office Centennial apps) on a device to which you have already deployed Microsoft 365 apps with Intune. If you install this configuration, it might cause data loss or corruption.
- Multiple required or available app assignments are not additive. A later app assignment will overwrite pre-existing installed app assignments. For example, if the first set of Office apps contains Word, and the later one does not, Word will be uninstalled. This condition does not apply to any Visio or Project applications.
- Multiple Microsoft 365 deployments are not currently supported. Only one deployment will be delivered to the device.
- Office version - Choose whether you want to assign the 32-bit or 64-bit version of Office. You can install the 32-bit version on both 32-bit and 64-bit devices, but you can install the 64-bit version on 64-bit devices only.
- Remove MSI from end-user devices - Choose whether you want to remove pre-existing Office .MSI apps from end-user devices. The installation won't succeed if there are pre-existing .MSI apps on end-user devices. The apps to be uninstalled are not limited to the apps selected for installation in Configure App Suite, as it will remove all Office (MSI) apps from the end user device. For more information, see Remove existing MSI versions of Office when upgrading toMicrosoft 365 Apps. When Intune reinstalls Office on your end user's machines, end users will automatically get the same language packs that they had with previous .MSI Office installations.
Select Microsoft 365 Apps
- Sign in to the Microsoft Endpoint Manager admin center.
- Select Apps > All apps > Add.
- Select Windows 10 in the Microsoft 365 Apps section of the Select app type pane.
- Click Select. The Add Microsoft 365 Apps steps are displayed.
Step 1 - App suite information
In this step, you provide information about the app suite. This information helps you to identify the app suite in Intune, and it helps users to find the app suite in the company portal.

- In the App suite information page, you can confirm or modify the default values:
- Suite Name: Enter the name of the app suite as it is displayed in the company portal. Make sure that all suite names that you use are unique. If the same app suite name exists twice, only one of the apps is displayed to users in the company portal.
- Suite Description: Enter a description for the app suite. For example, you could list the apps you've selected to include.
- Publisher: Microsoft appears as the publisher.
- Category: Optionally, select one or more of the built-in app categories or a category that you created. This setting makes it easier for users to find the app suite when they browse the company portal.
- Show this as a featured app in the Company Portal: Select this option to display the app suite prominently on the main page of the company portal when users browse for apps.
- Information URL: Optionally, enter the URL of a website that contains information about this app. The URL is displayed to users in the company portal.
- Privacy URL: Optionally, enter the URL of a website that contains privacy information for this app. The URL is displayed to users in the company portal.
- Developer: Microsoft appears as the developer.
- Owner: Microsoft appears as the owner.
- Notes: Enter any notes that you want to associate with this app.
- Logo: The Microsoft 365 Apps logo is displayed with the app when users browse the company portal.
- Click Next to display the Configure app suite page.
Step 2 - (Option 1) Configure app suite using the configuration designer
You can choose a method for configuring app setting by selecting a Configuration settings format. Setting format options include:

- Configuration designer
- Enter XML data
When you choose Configuration designer the Add app pane will change to offer three additional settings areas:
- Configure app suite
- App suite information
- Properties
- On the Configuration app suite page choose Configuration designer.
Select Office apps: Select the standard Office apps that you want to assign to devices by choosing the apps in the dropdown list.
Select other Office apps (license required): Select additional Office apps that you want to assign to devices and that you have licenses for by choosing the apps in the dropdown list. These apps include licensed apps, such as Microsoft Project Online desktop client and Microsoft Visio Online Plan 2.
Architecture: Choose whether you want to assign the 32-bit or 64-bit version of Microsoft 365 Apps. You can install the 32-bit version on both 32-bit and 64-bit devices, but you can install the 64-bit version on 64-bit devices only.
Update Channel: Choose how Office is updated on devices. For information about the various update channels, see Overview of update channels for Microsoft 365 Apps for enterprise. Choose from:
- Monthly
- Monthly (Targeted)
- Semi-Annual
- Semi-Annual (Targeted)
After you choose a channel, you can choose the following:
Remove other versions: Choose Yes to remove other versions of Office (MSI) from user devices. Choose this option when you want to remove pre-existing Office .MSI apps from end-user devices. The installation won't succeed if there are pre-existing .MSI apps on end-user devices. The apps to be uninstalled are not limited to the apps selected for installation in Configure App Suite, as it will remove all Office (MSI) apps from the end user device. For more information, see Remove existing MSI versions of Office when upgrading to Microsoft 365 Apps. When Intune reinstalls Office on your end user's machines, end users will automatically get the same language packs that they had with previous .MSI Office installations.
Version to install: Choose the version of Office that should be installed.
Specific version: If you have chosen Specific as the Version to install in the above setting, you can select to install a specific version of Office for the selected channel on end user devices.
The available versions will change over time. Therefore, when creating a new deployment, the versions available may be newer and not have certain older versions available. Current deployments will continue to deploy the older version, but the version list will be continually updated per channel.
For devices that update their pinned version (or update any other properties) and are deployed as available, the reporting status will show as Installed if they installed the previous version until the device check-in occurs. When the device check-in happens, the status will temporarily change to Unknown, however it will not be shown to the user. When the user initiates the install for the newer available version, the user will see the status changed to Installed.
For more information, see Overview of update channels for Microsoft 365 Apps.
Use shared computer activation: Select this option when multiple users share a computer. For more information, see Overview of shared computer activation for Microsoft 365 Apps.
Automatically accept the app end user license agreement: Select this option if you don't require end users to accept the license agreement. Intune then automatically accepts the agreement.
Languages: Office is automatically installed in any of the supported languages that are installed with Windows on the end-user's device. Select this option if you want to install additional languages with the app suite.
You can deploy additional languages for Microsoft 365 Apps managed through Intune. The list of available languages includes the Type of language pack (core, partial, and proofing). In the portal, select Microsoft Intune > Apps > All apps > Add. In the App type list of the Add app pane, select Windows 10 under Microsoft 365 Apps. Select Languages in the App Suite Settings pane. For additional information, see Overview of deploying languages in Microsoft 365 Apps.
- Click Next to display the Scope tags page.
Step 2 - (Option 2) Configure app suite using XML data
If you selected the Enter XML data option under the Setting format dropdown box on the Configure app suite page, you can configure the Office app suite using a custom configuration file.
Added your configuration XML.
Note
The Product ID can either be Business (
O365BusinessRetail) or Proplus (O365ProPlusRetail). However, you can only configure the app suite of the Microsoft 365 Apps for business edition using XML data. Note that Microsoft Office 365 ProPlus has been renamed to Microsoft 365 Apps for enterprise.Click Next to display the Scope tags page.
For more information about entering XML data, see Configuration options for the Office Deployment Tool.
Step 3 - Select scope tags (optional)
You can use scope tags to determine who can see client app information in Intune. For full details about scope tags, see Use role-based access control and scope tags for distributed IT.
- Click Select scope tags to optionally add scope tags for the app suite.
- Click Next to display the Assignments page.
Step 4 - Assignments
- Select the Required, Available for enrolled devices, or Uninstall group assignments for the app suite. For more information, see Add groups to organize users and devices and Assign apps to groups with Microsoft Intune.
- Click Next to display the Review + create page.
Step 5 - Review + create
Review the values and settings you entered for the app suite.
When you are done, click Create to add the app to Intune.
The Overview blade is displayed.
Deployment details
Once the deployment policy from Intune is assigned to the target machines through Office configuration service provider (CSP), the end device will automatically download the installation package from the officecdn.microsoft.com location. You will see two directories appearing in the Program Files directory:
Under the Microsoft Office directory, a new folder is created where the installation files are stored:
Under the Microsoft Office 15 directory, the Office Click-to-Run installation launcher files are stored. The installation will start automatically if the assignment type is required:
The installation will be in silent mode if the assignment of Microsoft 365 is configured as required. The downloaded installation files will be deleted once the installation succeeded. If the assignment is configured as Available, the Office applications will appear in the Company Portal application so that end-users can trigger the installation manually.
Troubleshooting
Intune uses the Office Deployment Tool to download and deploy Microsoft 365 Apps to your client computers using the Office 365 CDN. Reference the best practices outlined in Managing Office 365 endpoints to ensure that your network configuration permits clients to access the CDN directly rather than routing CDN traffic through central proxies to avoid introducing unnecessary latency.
Important
For custom Office Deployment Tool XML installs, the install status only reflects the result of the installation attempt. The install status does not reflect whether the app is currently installed on the machine.

Run the Microsoft Support and Recovery Assistant for Microsoft 365 on a targeted device if you encounter installation or run-time issues.
Additional troubleshooting details
When you are unable to install the Microsoft 365 apps to a device, you must identify whether the issue is Intune-related or OS/Office-related. If you can see the two folders Microsoft Office and Microsoft Office 15 appearing in the Program Files directory of the device, you can confirm that Intune has initiated the deployment successfully. If you cannot see the two folders appearing under Program Files, you should confirm the below cases:
The device is properly enrolled into Microsoft Intune.
There is an active network connection on the device. If the device is in airplane mode, is turned off, or is in a location with no service, the policy will not apply until network connectivity is established.
Both Intune and Microsoft 365 network requirements are met and the related IP ranges are accessible based on the following articles:
The correct groups have been assigned the Microsoft 365 app suite.
In addition, monitor the size of the directory C:Program FilesMicrosoft OfficeUpdatesDownload. The installation package downloaded from the Intune cloud will be stored in this location. If the size does not increase or only increases very slowly, it is recommended to double-check the network connectivity and bandwidth.
Once you can conclude that both Intune and the network infrastructure work as expected, you should further analyze the issue from an OS perspective. Consider the following conditions:
- The target device must run on Windows 10 Creators Update or later.
- No existing Office apps are opened while Intune deploys the applications.
- Existing MSI versions of Office have been properly removed from the device. Intune utilizes Office Click-to-Run which is not compatible with Office MSI. This behavior is further mentioned in this document:
Office installed with Click-to-Run and Windows Installer on same computer isn't supported - The sign-in user should have permission to install applications on the device.
- Confirm there are no issues based on the Windows Event Viewer log Windows Logs > Applications.
- Capture Office installation verbose logs during the installation. To do this, follow these steps:
- Activate verbose logging for Office installation on the target machines. To do this, run the following command to modify the registry:
reg add HKLMSOFTWAREMicrosoftClickToRunOverRide /v LogLevel /t REG_DWORD /d 3 - Deploy the Microsoft 365 Apps to the target devices again.
- Wait approximately 15 to 20 minutes and go to the %temp% folder and the %windir%temp folder, sort by Date Modified, pick the {Machine Name}-{TimeStamp}.log files that are modified according to your repro time.
- Run the following command to disable verbose log:
reg delete HKLMSOFTWAREMicrosoftClickToRunOverRide /v LogLevel /f
The verbose logs can provide further detailed information on the installation process.
- Activate verbose logging for Office installation on the target machines. To do this, run the following command to modify the registry:
Errors during installation of the app suite
See How to enable Microsoft 365 Apps ULS logging for information on how to view verbose installation logs.
The following tables list common error codes you might encounter and their meaning.
Status for Office CSP
| Status | Phase | Description |
|---|---|---|
| 1460 (ERROR_TIMEOUT) | Download | Failed to download the Office Deployment Tool |
| 13 (ERROR_INVALID_DATA) | - | Cannot verify the signature of the downloaded Office Deployment Tool |
| Error code from CertVerifyCertificateChainPolicy | - | Failed certification check for the downloaded Office Deployment Tool |
| 997 | WIP | Installing |
| 0 | After installation | Installation succeeded |
| 1603 (ERROR_INSTALL_FAILURE) | - | Failed any prerequisite check, such as:SxS (Tried to install when 2016 MSI is installed)Version mismatchOthers |
| 0x8000ffff (E_UNEXPECTED) | - | Tried to uninstall when there is no Click-to-Run Office on the machine |
| 17002 | - | Failed to complete the scenario (install). Possible reasons:Installation canceled by userInstallation canceled by another installationOut of disk space during installationUnknown language ID |
| 17004 | - | Unknown SKUs |
Office Deployment Tool error codes
| Scenario | Return code | UI | Note |
|---|---|---|---|
| Uninstall effort when there is no active Click-to-Run installation | -2147418113, 0x8000ffff or 2147549183 | Error Code: 30088-1008Error Code: 30125-1011 (404) | Office Deployment Tool |
| Install when there is MSI version installed | 1603 | - | Office Deployment Tool |
| Installation canceled by user, or by another installation | 17002 | - | Click-to-Run |
| Try to install 64-bit on a device that has 32-bit installed. | 1603 | - | Office Deployment Tool return code |
| Try to install an unknown SKU (not a legitimate use case for Office CSP since we should only pass in valid SKUs) | 17004 | - | Click-to-Run |
| Lack of space | 17002 | - | Click-to-Run |
| The Click-to-Run client failed to start (unexpected) | 17000 | - | Click-to-Run |
| The Click-to-Run client failed to queue scenario (unexpected) | 17001 | - | Click-to-Run |
Next steps
- To assign the app suite to additional groups, see Assign apps to groups.
Greetings!
As you all know, well-managed and secure remote access is a key aspect of Microsoft solutions. As most of us have seen, working remotely has taken on new scale and urgency right now and people across Microsoft have published some great reminders/guidance to help:
As a former IT Pro (and still one at heart), I know that during times of trouble, there is real value in having crisp, concise ‘just tell me what to do’ guidance. In this post, I’ll offer a ‘cut to the chase’ option for Intune that can help enable remote workers on BYO/unmanaged or 3rd party MDM-managed mobile devices with a minimum of impact to your current-state.
With any rapid-deploy change, there is heightened worry around the IT version of the Hippocratic Oath – ‘First, do no harm.’ This could be “Don’t blow up my end-user’s experience (nor my Helpdesk)” or, it could be, “Don’t drop my security posture to the floor.”
To that thought, I’m offering a “lighter hand” here – apply Intune MAM policy to Office Mobile Apps if/when they are used to access O365 content – but don’t block existing native app access, nor require device enrollment into Intune (think: personal device or existing 3rd party MDM).
- IMPORTANT: One of the goals of this post is to avoid impact to people already using the native apps on mobile devices to access O365. If you’re already blocking this, great – that is/was/continues to be our guidance. However, if you’re not there yet, this is a step towards that goal. Holistically, continue your work, driving towards a layered approach to security. This includes blocking legacy authentication, requiring managed apps, intelligent MFA, device-based trust, etc. The information offered here is a part of that ‘zero trust’ approach – but consider it just one piece of ‘low hanging fruit.’
Ok, let’s cut to the chase…
Scenario
Office 365 Intune Pricing
- Enable remote workers to create/update/save/collaborate on corporate content in O365 (SPO/OD/EXO) from un-managed mobile devices (BYO mobile phones and/or tablets) while reducing risks to that data
- Limit download/save as to a local device
- Limit cut/copy/paste to ‘un-managed’ apps
- Limit printing
- Require a PIN or biometric to open the Office Mobile Apps
- Enable selective wipe of corporate data from IT (via the Intune Portal) or the end user (if/when they remove the corporate account from the Office apps) – but don’t affect anything else on the device
- Such as photos, personal email, files, etc.
Solution: Apply controls to Office Mobile Apps on mobile devices
- Here, when the user signs in to the Office Mobile Apps with corporate credentials, the App “phones home” to your Intune MAM Service “back-end” and checks for any MAM Policies. If the user is targeted for any, the apps pull down the Policy settings and apply them.
- At that point (almost immediately), the app will notify the user that it’s now under policy control and the app will close.
- Intune MAM docs:
- MAM Without Enrollment reference – HERE
- MAM reference – HERE
- MAM settings reference – HERE
Solution Steps
- As always, you can/should use Groups to target/scope your rollouts – this could be a new or existing on-prem AD group that syncs to AAD or a CloudA self-service, pay-as-you-go model of providing computing resources to an organization or to the general public.
Cloud Computing evolved from existing technologies such as a fast and reliable Internet, virtual operating environments including virtual machines and virtual storage and is provided...More...' target='_blank'>cloud-only AAD group- Add your pilot users to that group
- You can easily use Group-based Licensing to ensure your users in the group have a required Intune license <HERE>
- Intune is included in the “E3” suites – M365 E3 or EMS E3.
- From the Intune Portal, create an “App Protection Policy” (APP) – aka “Mobile App Management” or MAM Policy – with a Name and Description…
- Select your target apps
- Select your data protection settings for cut/copy/paste and data encryption, etc. (the “i” tool-tip can help explain the options, or refer to our docs, link above)
- Select your app access requirements (such as a PIN for the apps, how often to re-enter the PIN, allow biometric instead of a PIN, etc.):
- Define your conditional launch settings:
- Assign your policy to the Group you created in Step 1
- Note – you can also use an ‘exclude’ group to further control targeting
- Review and complete the wizard:
Results
Now, when licensedIntune users in the targeted group sign-in to the Office Mobile Apps with their corporate creds, the MAM policy settings will apply to those apps and the corporate data within them.
For example, they’ll be prompted to setup an application-level PIN and will be blocked from cut/copy/paste of corporate data out of the policy-managed apps.
- “What does it look like for my end-users?”
- App PIN – This PIN can (should?) be different than the device PIN (however, we don’t have a control to force that – educate your end-users on that point)
- This can keep the kiddos out if they know your iPad PIN and use it to play Tetris, Space Invaders or even Pong (age-reference :smiling_face_with_smiling_eyes:)
- App PIN – This PIN can (should?) be different than the device PIN (however, we don’t have a control to force that – educate your end-users on that point)
- Prevent copy of ‘managed corporate data’ into local un-managed applications
- Prevent Save as to un-managed locations (Files App or ‘On My iPad” is blocked; SharePoint Online and OneDrive for Business is managed/allowed):
You can now ‘encourage’ your users to install/use the Office Mobile Apps when accessing O365 and know that the corporate data will be well-protected.
Remember, in this specific case, we’re trying to ‘do no harm,’ so we “encourage” vs “require” …
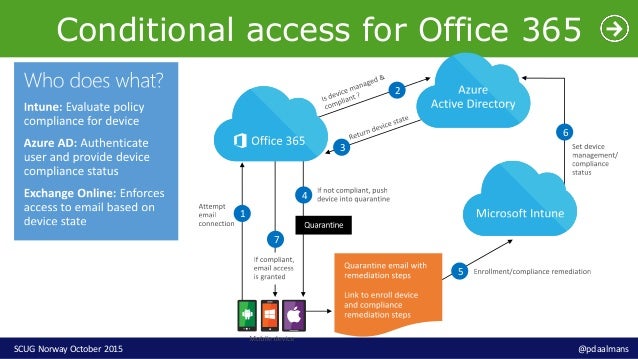
- Of course, recall from the beginning of the post, you could use (and should consider) Azure AD Conditional Access, and other controls for layers of security for more stringent access control:
- Block (or limit) “the un-managed” – personal devices, native mail clients/apps that don’t support MAM Policies
- Require “the managed” – MDM devices, Office Mobile Apps/other apps that support MAM Policies
Notes/FAQs
- As mentioned, this solution does NOT require Intune-enrolled devices; they can be un-managed or even managed by a 3rd party MDM.
- It does require an Intune license for the users in your target group, though.
- There are additional/other access control capabilities in M365, such as AAD Conditional Access, Microsoft Cloud App Security (MCAS) and others, but this specific configuration is super quick and easy – and pretty low-risk on the ‘do no harm’ scale.
- “What if users already have Outlook Mobile on their devices and their personal email account defined?”
- No problem – we leave the personal email accounts alone both during policy application and if/when the app is selectively wiped (either by IT or by the end-user removing the corporate account from the app)
Microsoft Mobile Device Management
- iOS users may be prompted to install the Microsoft Authenticator app on a BYO device
- For instance, if you have existing app-based Conditional Access Policies setup in Azure AD that require device registration in AAD, iOS uses the MS Authenticator App to perform the device registration in AAD
- Android users will be required to install the Microsoft Intune Company Portal app (if they don’t have it already installed)
- They don’t need to enroll the device into Intune, though, only install the app – ensure you educate your users/helpdesk on this point.
Office 365 Mdm Vs Intune
- While this model of using Intune MAM is generally pretty ‘low impact’ (no blocking access), you should always do your due diligence and test your specific scenarios, in your specific environment, with your current configs and device types. Be sure to pilot the roll-out and control the ‘pace of change’ – even if it’s faster than normal.
- These policies are ‘scoped’ to groups – you can/should start with a group of a few users to validate the results/behavior.
- As you gain comfort with the results, expand the group members at the speed of your org’s choosing/comfort:
- 5-10 users > 20-100 users > 250-1000 users … ?
If you need/want more assistance, you have several options:
- Microsoft Fast Track – anyone with 150+ licenses can use the Fast Track Center to request assistance/guidance. <HERE>
- Microsoft Premier Services/Microsoft Consulting Services/Unified Support – anyone with a Premier or Unified Support contract can reach out for help – contact your Technical Account Manager (TAM) or <HERE>
- Microsoft Partners – if you are working with a Microsoft Partner, hit them up – They’re always willing to help.
- Our own docs – <HERE>
Best of luck as we all work through these “highly-uncertain” of uncertain times!
Office 365 Intune
Hilde
