The IP address of your Meraki MX. Only clients with configured addresses and shared secrets will be allowed to send requests to the Authentication Proxy. Radiussecret1: A secret to be shared between the proxy and your Meraki MX. Jan 19, 2021 Is this a Meraki MX being used for the VPN? As you can use the same Windows AD username and password if you have set up a radius server to authenticate. In the Meraki VPN connection guide for Windows it specifies that the Miniport adaptor settings have to be set in Windows 10. But you are already getting it to connect which is strange. There are three options for configuring the MX-Z's role in the Auto VPN topology: Off: The MX-Z device will not participate in site-to-site VPN.; Hub (Mesh): The MX-Z device will establish VPN tunnels to all remote Meraki VPN peers that are also configured in this mode, as well as any MX-Z appliances in hub-and-spoke mode that have the MX-Z device configured as a hub.
Cisco Meraki’s unique auto provisioning site-to-site VPN connects branches securely, without tedious manual VPN configuration. Leveraging the power of the cloud, MX Security Appliances configure, monitor, and maintain your VPN so you don't have to.
Cisco Meraki’s unique auto provisioning site-to-site VPN connects branches securely with complete simplicity. Using IPsec over any wide area network, the MX links your branches to headquarters as well as to one another as if connected with a virtual Ethernet cable. Customers accessing or moving services to the Amazon Web Services cloud can use Auto VPN to connect directly to a virtual MX inside their Virtual Public Cloud.
MX Security Appliances automatically configure VPN parameters needed to establish and maintain VPN sessions. A unique cloud-enabled hole-punching and discovery mechanism enables automatic interconnection of VPN peers and routes across the WAN, and keeps them updated in dynamic IP environments. Security associations and phases, authentication, key exchanges, and security policies are all handled automatically by MX VPN peers. Site-to-site connectivity is established through a single click in the Cisco Meraki dashboard. Intuitive tools built in to the Cisco Meraki dashboard give administrators a real-time view of VPN site connectivity and health. Round trip time latency between peers and availability status information automatically keep track of all the VPN peers in the network.

Mxvpn Download
Flexible tunneling, topology, and security policies
Configurations for split-tunneling and full-tunneling back to a concentrator at headquarters are fully supported and configured in a single click. Hub-and-spoke and full mesh VPN topologies give deployment flexibility, and a built-in site-to-site firewall enables custom traffic and security policies that govern the entire VPN network.
Cloud Managed Security Appliances
See features, specifications, and pricing for Cloud Managed Security Appliances.
Posted by: Emily Sporl
Customers who run multiple Cisco Meraki MX Security Appliances in their networks already enjoy effortless site-to-site VPN between them. But often, remote sites using non-Meraki VPN peers need to be assimilated into these VPN networks. We were thrilled to announce a new feature that gives IT administrators more flexibility in configuring Phase 1 and Phase 2 parameters of these third-party connections. Now, we’ve extended that flexibility to allow Meraki customers control over which Meraki MX or Z1 networks connect to specific third-party peers.
For example, suppose a large, distributed medical organization manages hundreds of hospitals that are securely connected via meshed Meraki site-to-site VPN, all sharing resources. Let’s say that this medical organization must securely connect with an external firm—which does not use Meraki MX Security Appliances—to back up electronic medical records from specific hospitals. With MX VPN tagging, only the specific hospital networks needing backups would be made available to the external firm.
Meraki Vpn Settings
How it works
If customers have tagged their Meraki networks, they can make third-party VPN peer connections available based on these tags. Before (and by default), these third-party peer connections were available organization-wide. To restrict VPN availability, simply select the Meraki network tags that should have access to remote, third-party VPN sites; any Meraki network not suitably tagged will not have VPN access to these sites.
Configuring non-Meraki peer VPN settings and allowing this connection based on tag.
To tag a Meraki network, simply navigate to Organization > Overview in the Meraki dashboard and select one or more networks to tag. Then click the “Tag” button at the top left corner of the network listing table, and add, remove, or create a new tag.
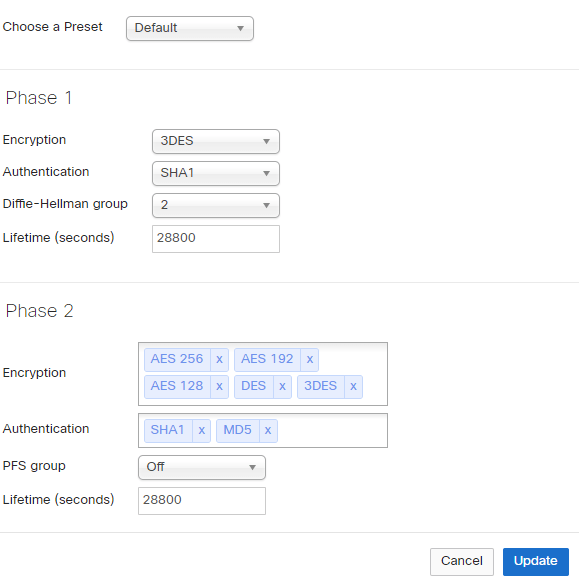
This feature greatly enhances flexibility and control in managing non-Meraki VPN peers in a hybrid VPN network. We’d be excited to hear what you think, so please don’t hesitate to drop us a line or make a wish!

Related Posts
